- Home
- Product updates
Product Updates
See what’s new at our product, check the updates below
- 229 Product updates
NewsOct 20, 2022
Devo Platform 7.16 Released!
We are very proud to announce Devo Platform Release 7.16 with two long awaited and requested features! Region Status CA Released US Released EU Rolled into 7.17 APAC Released New Features Data Search: List View Data Search: New Smart Query Code Editor Data Search: New Copy Option Application: Auto Admin Role New Features Data Search: List ViewList View!This alternative data view displays information of an event as a list of keys and values known as pills. This new view displays the information in two columns: the eventdate and the list of keys and values. You can freely switch between both views with a speed that must be experienced!See this new view in use in this short video! Data Search: New Smart Query Code EditorSmart Query BuildingWe have simplified the task of writing LINQ queries with this new smart editor. As you type it will autocomplete table names, field names and much more! Building a search will be easier, faster and more convenient than ever! Data Search: New Copy OptionNew Copy OptionsBoth Tabular and List views can take advantage of new copy options when you right click on the data. You can see it in action here in this video.New Copy functions in Action! Application: Auto Admin RoleThis quality of life improvement will apply admin role to any new applications installed automatically. Previously it was necessary to assign the the role manually. Additional Improvements to the UI, and Bug Fixes can be found in the full release notes.Documentation page for 7.16 full release notes Let us know what you like about this release!
Related products:Devo Platform
NewsOct 12, 2022
Security Operations 3.07.1 Released
Hello Everyone! SecOps version 3.7.1 has been released with some great quality of life updates! Lets take a look!Check out the full details in our Documentation Page. Region Status CA Released US Released EU Released APAC Released Note: SightingDB has been depreciated and removed due to limited usage of this enrichment. It is no longer shown in settings. Key FeaturesImpact Calculation Multiple Priority Selection Bulk Changes in Alert Status Impact CalculationYou can now disable Impact Calculations to improve performance. Multiple Priority SelectionYou can now select two or more priorities at the same time to filter alerts! Bulk Changes in Alert StatusYou can now change the status of a given alert group, including Add to Investigation & Change Status actions. And more importantly Closed Status! Enjoy!
Related products:Devo SecOps
NewsOct 12, 2022
Release 8 Out of The Box Alerts
Hello All!The Devo Threat Research Team has just released their October OOTB Alerts for you! This release, available now from the SecOps Content Manager, provides 13 new Linux, Mimecast and Google Workplace out-of-the-box detections.One alert has been updated as well!Get the full details in our Documentation Page! Devo is committed to providing high quality alerts for all customer environments. In our upcoming release we will continue to take a closer look at some of our more “noisy” alerts and tune them to help with performance.
Related products:Devo SecOps

NewsOct 11, 2022
Devo Exchange Use Cases: DoS, McAfee and Port Scan
Devo Exchange has a new content type called Use Cases. Use Cases combine a data injection with an Activeboard or Alert to reproduce a particular use case. You can use it to gain experience, fine tune your alerts and increase your workflow efficiency.Watch the Use Case Launch Video! Each component of a Use Case can be downloaded separately as well if you have your own data already or want to test your own Activeboard creations. Launching with 3 initial use cases, the team will be updating this section of Devo Exchange with more use cases in the future. Please let us know if you have a use case you want them to create!Denial of Service Use Case McAfee Monitoring Use Case Port Scan Use CaseDenial of Service Use CaseA Denial of service attack (DoS) is a cyber-attack in which the perpetrator seeks to make a machine or network resource unavailable to its intended users by temporarily or indefinitely disrupting services of a host connected to a network. This Use Case includes a Firewall Data Injection for DoS and the DoS Detection Alert Pack. Download it from Devo Exchange! McAfee Monitoring Use CaseGet experience with the McAfee Activeboard in this Use Case. This use case allows you to visualize the full McAfee Activeboard, gain experience and see where to fine tune your reporting.This Use Case includes Proxy data Injection for McAfee and the Proxy McAfee Monitoring Active Board.Watch the Guided tour! Download it from Devo Exchange! Port Scan Use CaseA port scan is a common technique hackers use to discover open doors or weak points in a network. A port scan attack helps cyber criminals find open ports and figure out whether they are receiving or sending data. It can also reveal whether active security devices like firewalls are being used by an organization. This Use Case includes a Firewall Data Injection for Port Scan and Port Scan Detection Alert Pack.Download it from Devo Exchange! Please let us know if you have a use case you want the team to create!
Related products:Devo Exchange

NewsOct 11, 2022
Devo Exchange: End Point Agent Monitoring Activeboard
The Endpoint Agent monitoring Activeboard provides visibility of the data received from the Endpoint Agent fleet deployed in your environment. The Endpoint Agent solution builds on top of Osquery and FleetDM, and providing real time visibility and rich information that span through configuration, execution status or performance. The Activeboard implements four use cases: Fleet overview: Active of endpoints and managers, configuration and status Data retrieval processes: Configured packs, queries and associated ingestion data (events, volumes, etc.) Alerts: Summary of alerts triggered on Endpoint Agent data Endpoints status drill-down: latest events and configuration details The Activeboard is configured to generate a consolidated view of the agents fleet, but also permits a highly granular access to the data through the usage of multi-criteria filtering options. Download now from Devo Exchange!
Related products:Devo Exchange

NewsOct 4, 2022
Devo Exchange: Alert Pack: MS Exchange RCE (ProxyNotShell)
The Devo Exchange Team in collaboration with Devo’s SciSec Team have published a new Alert Pack as part of the coordinated response to the ProxyNotShell 0-Day Vulnerability in Microsoft Exchange.This pack contains 3 Alerts hand crafted by the SciSec Team to check your environment for this dangerous exploit. These areSecOpsProxyNotShellHashIoc SecOpsProxyNotShell SecOpsProxyNotShellIpIocDownload this Alert Pack directly from Devo Exchange. Learn more about This Alert pack in our docs! Additional Resources Devo SciSec Team Blog on ProxyNotShell.MITRE ATT&CK Analysis on this type of attack
Related products:Devo PlatformDevo Exchange

Oct 4, 2022
Devo Exchange: Firewall Monitoring
New ActiveBoard released in Devo Exchange! Firewall MonitoringThis Activeboard is based on firewall.all.traffic table and allows you to analyze and monitor firewall traffic logs from different angles. In this activeboard you will be able to:Get data insights about Action, Protocol, Source Zone, Source IP, Source Port, Device Name, Application, Destination Zone, Destination IP, Destination Port and you will be able to filter the widgets by those Track Traffic Volume and Actions Have access to Traffic Reputation heatmaps by Source and Destination Compare the top 10 connections by source IP, the top 10 data volume for each source IP and each destination IP, and the top Talkers by connection and by data transfer... Get details about the most used Firewall rules Analyze denied firewall traffic and most rejected source IPsNote: This Activeboard processes a large amount of data. It is highly recommended you use aggregation tasks to speed up loading and processing. Learn more here: https://docs.devo.com/space/latest/95207931/Manage+widgetsDownload it today! Download directly from Exchange. How to install Exchange content.
Related products:Devo PlatformDevo Exchange
NewsSep 19, 2022
Devo Product 7.15 Released!
We are pleased to announce the Devo Platform Release 7.15 is now starting to roll out to all Geos! We have a lot of great stuff in this release, so lets go over it all. See the full release notes in our Docs here. Currently Available in :Region Status CA Released US Released EU Released APAC Pending Multitenancy Data Access across domains Activeboards gets New Widget and API New Timelapse Widget: Timelapse Query Activeboards API: Additional Activeboard Updates Copying Widgets to other Activeboards New Predefined Global Variables Usability Improvements User Identification via email addresses Improved Activeboard role-sharing reporting New Relay API: New Provisioning API Methods Advanced password processing: Also in this ReleaseMultitenancy Data Access across domainsThe Devo Platform’s multitenancy capability enables users to centrally provision, monitor, manage, and query an unlimited number of tenants. MSSPs and large enterprises can maintain complete visibility into the data they manage while safeguarding its privacy and security, maintaining the residency and compliance requirements of their data.Watch this video to learn more about Devo’s multitenancy capability. Activeboards gets New Widget and APINew Timelapse Widget:Timelapse in action The Timelapse widget gives users the ability to capture data across specific timeframes. Users can graphically compare different time ranges in one data series, which helps them visually analyze and predict behaviors, improving incident detection and resolution times.Watch this video for a more detailed description of how it works. Timelapse QueryThe timelapse query defines the series to be analyzed. The query consists of a timestamp column, the event time reference, and a numeric column containing the value to be compared. Activeboards API:Devo users can now build and export Activeboards via a web-based REST API, which enables customization and portability. Users can quickly share Activeboards and generate reports, increasing productivity and improving customer satisfaction. View all the details in our Docs. Additional Activeboard UpdatesCopying Widgets to other ActiveboardsUsers now can copy a widget into a clipboard and paste it into the same Activeboard, a different Activeboard, or another program as configurable text.New Predefined Global Variables The Activeboard language contains the following variables, which are helpful for widget queries. Domain_name Domain_id User_name User_email User_id Activeboard_name Activeboard_id Locale Timezone Isolated Usability Improvements User Identification via email addressesUsers are now identified in the Activeboard manager by their email addresses. This simplifies administration capabilities since email names are unique.Improved Activeboard role-sharing reportingAdministrators can now view and set permissions that enable users to view and edit Activeboards across predefined roles in the organization. New Relay API:Users can access relays via a REST API to manage relays and check their status. This gives users access to relays without having to log into the Devo domain. Additionally, users can use the API to clone relay rules from one domain to another, which improves efficiency.Read more about the Relay API in our Docs. New Provisioning API MethodsDevo has added new methods in the Provisioning API. This is meant to make administering multiple domains easier for MSSPs. Now users can manage domain limits and domain preferences via API using: Manage domain limits: user limits, cert limit, key limit Manage domain preferences: Generic preferences: default language, session expiration timeout Data search preferences: real-time ON/OFF, default time frame, default case sensitivity Advanced password processing:Improved complexity requirements have been added for new passwords. These updated validation rules apply when recovering, changing, or setting new passwords, which improves the security of your Devo domain. Also in this ReleaseDevo Platform Release 7.15 also contains new Activeboards features such as enhanced user identification, improved data formatting, and additional accessibility settings, which enhance usability and boost productivity. See the full release notes in our Docs here.
Related products:Devo Platform
NewsSep 14, 2022
Security Operations Application Release 3.4.0
The Security Operations team is happy to announce the release of version 3.4 of the Security Operations Application for the Devo Platform.Region Status CA Released US Released EU Released APAC Released Primary focus for this release has been on bug fixes, as well as accelerating the retrieval of the results in the Associations workbench between events and reducing the amount of latency in visualizing the information requested. This is the first of the many backend improvements planned by SecOps to provide the SOC team with the right capabilities to perform their job quickly and efficiently. Full Release notes available in Docs here. SummaryImprovements to Enigma: Entities and Vertical Applications: Adaptations for Entities.Bug FixesList of Multi Lookups contained several entries which where no longer in use. The MISP indicator has been added to the Content Manager.
Related products:Devo SecOps
NewsSep 8, 2022
Release 7 - Out of the Box Alerts
Hello Everyone! We are glad to announce that the Devo Threat Research team has released the latest batch of detections to the SecOps content manager. In this release, we have created new detections for one of the most popular operating systems; Linux. Linux is very important to have monitored because it is used by 50% (more than Mac) of professional developers worldwide and is an asset to most companies. These alerts will help our customers become notified of any potential attacker or modification to basic directories and production level servers, including the creation of hidden directories and files. Click here to view the full release notes in our Docs portal. With this release we are now at a total of 401 out of the box detections, with our goal of hitting 500 by end of the year.The Devo Threat Research team is committed to keeping its monthly cadence of releases to deliver new and exciting content to our security customers. More from the team soon!
Related products:Devo Platform

NewsSep 8, 2022
Alert Pack: Command and Control Released for Devo
The Devo SciSec Team (Devo’s Threat Research Team) has released this latest alert pack in all Devo domains! This alert pack brings our SecOps related content to our non-SecOps customers and can help jumpstart your threat coverage. Alert Pack - Command and ControlThis alert pack focuses on providing coverage for the most commonly used attacks for the Command and Control Mitre Attack tactic. Command and control is used when the adversary has your system under control and is trying to steal, or disrupt. information from your company. These alerts will let our customers know when the attacker tries to seize control, use their control, or try to control more systems. Here's more information from the Mitre website: Complete information on this threat vector. "Command and Control consists of techniques that adversaries may use to communicate with systems under their control within a victim network. Adversaries commonly attempt to mimic normal, expected traffic to avoid detection. There are many ways an adversary can establish command and control with various levels of stealth depending on the victim’s network structure and defenses." Download now directly from Devo Exchange by clicking here. Full release notes and details of every alert in this Alert Pack. Here is a sample of a few of the alerts included:SecOpsFWSMBTrafficOutbound - Detects SMB traffic from internal to external sources allowed through the firewall.SecOpsFWTrafficOnUnassignedLowPort - Identifies traffic across a port lower than 1024 that is unassigned by IANA. These ports are rarely used by legitimate services and may indicate malicious activity or traffic.SecOpsFWExcessFirewallDeniesOutbound - Detects excessive firewall blocks for outbound traffic from a single IP in a short period of time; this activity may be indicative of C2 traffic and should be reviewed.SecOpsFWIcmpExcessivePackets - Since ICMP packets are typically very small, this alert will detect ICMP packets that are larger than expected. A large amount of data sent over ICMP may indicate the presence of command and control traffic or data exfiltration.SecOpsFWRdpTrafficUnauthorized - Detects RDP traffic to hosts, not within an allowed list. Full list alerts available here in our docs!
Related products:Devo Platform
NewsSep 1, 2022
Python SDK v4.0.2 Released
We are glad to announce that Python SDK v4.0.2 has been released. This is a patch release and includes the following:Add a new command-line option for escaping double quotes with -eq or --escape_quotes. Add a check and shows a warning if the file contains double quotes and the option -eq is not used. Add a new command-line option in tests for testing just one module with -m <module_name> or --module <module_name>.Check the package at https://pypi.org/project/devo-sdk/The source code is available on GitHub: https://github.com/DevoInc/python-sdk
Related products:Devo Platform

NewsSep 1, 2022
Alert Technology Pack: Proxy Released for Devo
The Devo SciSec Team (Devo’s Threat Research Team) has released this technology alert pack in all Devo domains! This alert pack brings our SecOps related content to our non-SecOps customers and can help jumpstart your threat coverage. Download now directly from Devo Exchange by clicking here. Alert Technology Pack - ProxyThis Proxy pack provides our customers with detections to help them from even the most dangerous of threats. This pack is extremely important based on the role that the Proxy plays in most organizations. That's why we knew that we needed to have alerts dedicated to alerting when an attacker has disabled or gotten past the proxy. Full release notes and details of every alert in this Alert Pack. SecOpsNonStandardHTTPMethod - HTTP defines a set of request methods to indicate the desired action to be performed for a given resource. It is necessary to monitor the non-standard methods used in web servers queries because this could indicate an attack.SecOpsMultipleHTTPMethodsUsed - There are more than ten HTTP Methods but usually clients use a few only. If a client uses all of them or a large number of methods, this could be recon, probing, or enumeration.SecOpsUserBlockedbyProxy - It is considered suspicious that a user is blocked by a proxy server on many occasions in a short period of time.SecOpsProxyLargeFileUpload - Identifies file uploads above 50 MB in size. Excessive file uploads may indicate exfiltration by an adversary or insider. The size threshold should be tuned per organization.SecOpsPortIntoURL - During the normal navigation of a user or system, the URLs do not include the destination port. The use of the port could be seen as suspicious behavior when combined with other factors. Full list available in our docs here.
Related products:Devo Platform

NewsAug 30, 2022
Alert Pack: Impact Released for Devo
The Devo SciSec Team (Devo’s Threat Research Team) has released our fourth alert pack in all Devo domains! This alert pack brings our SecOps related content to our non-SecOps customers and can help jumpstart your threat coverage. Alert Pack - ImpactWe have another alert pack focused on the MITRE Attack tactic Impact. Impact is a tactic that is used by attackers to disrupt and incur damages to a company. Worst of all these attacks can cause reputational damages which can take years to recover from. That's why we knew we had to create an alert pack to protect our customers from these issues. Here's more information from the MITRE organization. Complete information on this threat vector. "Impact consists of techniques that adversaries use to disrupt availability or compromise integrity by manipulating business and operational processes. Techniques used for impact can include destroying or tampering with data. In some cases, business processes can look fine, but may have been altered to benefit the adversaries’ goals. These techniques might be used by adversaries to follow through on their end goal or to provide cover for a confidentiality breach." Download now directly from Devo Exchange by clicking here. Full release notes and details of every alert in this Alert Pack. Here is a sample of a few of the alerts included:SecOpsAzureNWDeviceModified - This alert identifies when a user has modified a network device such as network virtual appliance, virtual hub or virtual router. Although this is a common operation, it should be checked since it could be undermining the security posture of the Azure account.SecOpsAzureAutomationRunbookDeleted - This alert identifies when a user has deleted an Azure Automation runbook. This could be indicative that an attacker may be trying to disrupt the normal behavior of the automated processes within an azure account or deleting a runbook used in order to gain persistence.SecOpsGCPSQLDatabaseModification - An attacker could intend to modify, or gain, privileges on a Cloud SQL Database.SecOpsGCPPrivateCloudNetworkDeletion - An attacker could delete a Virtual Private Cloud Network (VPC) to interrupt availability of systems and network resources.SecOpsGCPIAMServiceAccountDisabled - An adversary could disable an IAM Service Account to manipulate the service account and maintain access to the systems. Full list alerts available here in our docs!
Related products:Devo Platform
NewsAug 29, 2022
Python SDK v4.0.1 Released
We are glad to announce that Python SDK v4.0.1 has been released. This is a patch release and includes the following:Running tests whenever a pull request is created, recreated, or synchronized in GitHub. Running a task to publish in PyPI when a new release is made in GitHub. Deprecation of unsupported Python versions. Verification of some CSV cases. Automatization of badges shown in GitHub and PyPI.Check the package at https://pypi.org/project/devo-sdk/The source code is available on GitHub: https://github.com/DevoInc/python-sdk
Related products:Devo Platform

NewsAug 24, 2022
Alert Technology Pack: Azure Released for Devo
The Devo SciSec Team (Devo’s Threat Research Team) has released this Technology alert pack in all Devo domains! This alert pack brings our SecOps related content to our non-SecOps customers and can help jumpstart your threat coverage. Full release notes and details of every alert in this Alert Pack. Alert Technology Pack: AzureMicrosoft Azure is used for all kinds of projects and initiatives for our customers, the importance of being aware of any potential issues cannot be understated.Devo is one of the market leaders in Out Of The Box Azure alerts with one of the highest number of detections at highest levels of alert quality. These detections protect all aspects of Azure ranging from Active Directory to DevOps. We want to ensure that our customers are accurately covered and can rest assured that these detections will alert them for most attacks they face. Download now directly from Devo Exchange by clicking here. Here is a sample of 5 of the alerts in this pack:SecOpsAzureExternalUserInvited - An adversary could create an invitation for an external user to create a new account in Azure AD. This may be a routine activity but could be used as a vector for an adversary to gain access or persistence.SecOpsAzureUserInformationDownload - An adversary may attempt to get a listing and more information about accounts on a system or within an environment.SecOpsAzureImpossibleTravel - An adversary could obtain and abuse credentials of existing accounts as a means of gaining Initial Access. Compromised credentials may be used to bypass access controls and for persistent access to remote systems and external services.SecOpsAzureUserCreated - An adversary could attempt to persist by creating a user account in Azure AD.SecOpsAzureUserLoginSuspiciousRisk - An adversary could obtain and abuse credentials of existing accounts as a means of gaining Initial Access, Persistence, Privilege Escalation, or Defense Evasion.
Related products:Devo Platform

NewsAug 22, 2022
Alert Pack: Firewall Released for Devo
The Devo SciSec Team (Devo’s Threat Research Team) has released this Technology Alert Pack in all Devo domains! This alert pack brings our SecOps related content to our non-SecOps customers and can help jumpstart your threat coverage. Full release notes and details of every alert in this Alert Pack. Technology Alert Pack - FirewallInside this alert pack you will find a plethora of detections that will alert when an attacker is attacking or trying to bypass a firewall. These alerts are incredibly important to let our customers know when they could be a breach!Firewalls are one of the last bastions of defense for your company, and any firewall that gets compromised can lead to an open highway for attackers to use to gain entry into your environments. In order to ensure a more comprehensive security outlook, Devo’s detections provide the extra assurance that any crack in the wall will be made aware to your SOC and your company. Download now directly from Devo Exchange by clicking here. Here is a sample of 5 of the alerts in this pack.SecOpsFWIpScaninternal - Detects when a single internal IP is scanning other internal IPs using different ports for each scan attempt. This is a low and slow technique intended to avoid triggering traditional port scan and port sweep alerts.SecOpsFWSigned - Detects exploitation of DNS RCE bug reported in CVE-2020-1350 by monitoring for suspicious outbound DNS traffic over TCP. The destination name server should be examined for legitimacy.SecOpsFWRdpTrafficUnauthorized - Detects RDP traffic to hosts, not within an allowed list.SECOpsVNCPortOpen - Possible VNC Connections.SecOpsFWRDPExternalAccess - Identifies RDP traffic from external sources allowed through the firewall. This type of traffic may indicate an adversary is in possession of valid accounts and is accessing a host from outside the network.
Related products:Devo Platform
NewsAug 10, 2022
Release 6 - Out of the Box Alerts
Sec-Ops is proud to present Release 6! Chock full of Out of the Box Alerts.The Devo Threat Research team has released a new set of detections to our customers. In Release 6, we are releasing new detections spread across Office 365, Microsoft Azure, Windows, and now Linux technologies. These data sources are among some of the largest ingested into Devo and help protect our customers against common attacks. Release 6 brings the Security Operations Out Of The Box alerts total to 385 signature based detections with hundreds more on the way. Full release notes and details of every alert in this Alert Pack. Here is a sample of 5 of the new Alerts:Detects a GetSecretValue action where the source IP does not belong in an Amazon instance IP space. Detects the deletion of Web Server access logs. Detects the deletion of sensitive Linux system logs Detects the deletion of SSH Key. Detects for suspicious setcap utility execution to enable SUID bit.Check out the full release notes here.
Related products:Devo SecOps

Aug 5, 2022
Alert Pack - Execution for Devo
The Devo SciSec Team (Devo’s Threat Research Team) has released our fourth alert pack in all Devo domains! This alert pack brings our SecOps related content to our non-SecOps customers and can help jumpstart your threat coverage. Alert Pack - ExecutionThis release brings a multitude of detections that will alert when an attacker is trying to execute malicious scripts and malware. These alerts will provide your team with actionable information on attacks using keylogging scripts, downloading malware, etc. all types of attacks that are trying to keep your system down or steal information. Complete information on this threat vector. “Execution consists of techniques that result in adversary-controlled code running on a local or remote system. Techniques that run malicious code are often paired with techniques from all other tactics to achieve broader goals, like exploring a network or stealing data. For example, an adversary might use a remote access tool to run a PowerShell script that does Remote System Discovery.” Download now directly from Devo Exchange by clicking here. Full release notes and details of every alert in this Alert Pack. Here is a sample of a few of the alerts included:SecOpsO365PowerShellActivity - This alert catches uses of PowerShell in the O365 environment.SecOpsWinExecVbsScript - Detects suspicious file execution by wscript and cscript. Adversaries can use this mechanism to execute malicious code for persistence or privilege escalation.SecOpsWinSchtasksRemoteSystem - Detects flags passed to schtasks.exe on the command-line that indicate a job is being scheduled on a remote system.SecOpsWinScheduledTaskCreation - Detects when a scheduled task is created in Windows.SecOpsAzureAutomationWebhookCreated - This alert identifies when an Azure Automation webhook has been created. This could be leveraged by an attacker in order to execute arbitrary code on the Azure environment.
Related products:Devo Platform

NewsAug 4, 2022
Alert Pack - Initial Access for Devo
The Devo SciSec Team (Devo’s Threat Research Team) has released our third alert pack in all Devo domains! This alert pack brings our SecOps related content to our non-SecOps customers and can help jumpstart your threat coverage. Alert Pack - Initial AccessThis release brings a multitude of detections that will alert when an attacker is using common initial access tactics. These alerts will provide your team with actionable information as soon as the attackers attempt to gain access to your environments and attempt to start making longer lasting impacts to your systems. Complete information on this threat vector. “Initial Access consists of techniques that use various entry vectors to gain their initial foothold within a network. Techniques used to gain a foothold include targeted spearphishing and exploiting weaknesses on public-facing web servers. Footholds gained through initial access may allow for continued access, like valid accounts and use of external remote services, or may be limited-use due to changing passwords.” Download now directly from Devo Exchange by clicking here. Full release notes and details of every alert in this Alert Pack. Here is a sample of a few of the alerts included:SecOpsO365PhishAttempt - Adversaries may send victims emails containing malicious attachments or links, typically to execute malicious code on victim systems.SecOpsWinAdminRemoteLogon - Detects remote logins by an administrative user account. Administrative account names are tailored to the organization's specific naming conventions.SecOpsProofpointTAPUserReceivedMalwareEmail - Proofpoint TAP detected a user receiving an email with a malware score of 75 or higher. Records indicating the email was permitted will have a higher signal score compared to those automatically blocked by Proofpoint.SecOpsAWSRootLogin - This detection filters by cloudtrail events with ConsoleLogin as eventName and userName equal to root.SecOpsO365PowerShellActivity - This alert catches uses of PowerShell in the O365 environment.
Related products:Devo Platform
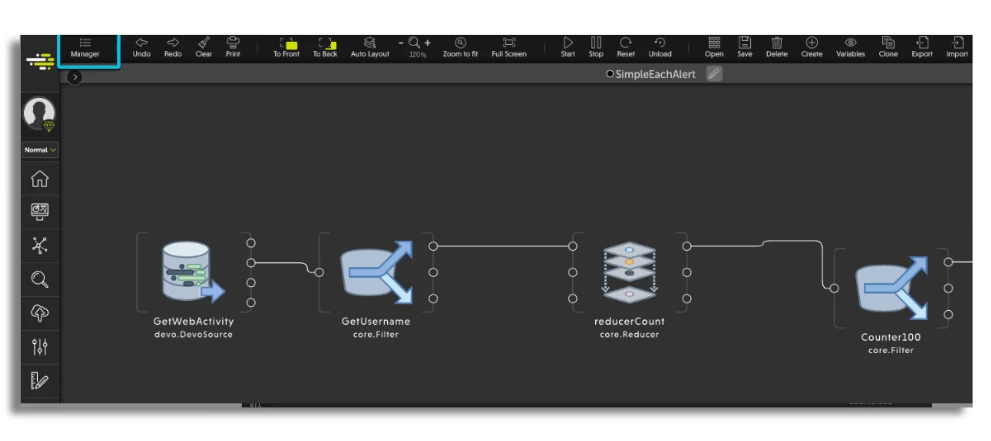
Jul 29, 2022
Devo Adds New Flow Manager and Additional Enhancements to Flow Release 1.13
We are pleased to announce Devo Flow 1.13. Read on to learn what’s new!Where is it releasedRegion Status CA Released US Released EU Pending APAC Pending New Welcome PageDevo has added a new Flow Welcome Page, which can be found on the Flow home screen when:Flow is opened for the first time There are no open tabs The Flow Welcome Page is a launch point for the tool and also highlights popular use cases, the latest training videos, and helpful resources. Learn more here. Options include:Start/Open/Import a flow Go to the Flow Management Dashboard Navigate toward recently opened flows Access useful resources Learn the basics of Flow New Flow Manager Devo has added a new Flow Manager. Learn more here. Users with flow domain rights can view and manage all the current flows within that domain. Users with their own flow rights can view and manage the flows within their domain Available capabilities: Load all flows in different tabs (in bulk) Search flows by name Filter flows by different fields Order flows by Status, Date, and Creator Take individual actions for each flow start, stop, load, remove, clone New Manage and Back Buttons The Manage button directly navigates from the Flow workspace to the Flow Manager.The Back button returns to the previous page from within the Flow Manager Rabbit Unit Improvements The following fixes and enhancements have been implemented for the Rabbit Unit. For more details about the Rabbit Receiver Unit, please refer to the Devo Documentation.Add a queue name when reading from an “exchange”. This makes it possible to read messages from the same temporary queue from multiple units, which distributes the load Bug fix: When restarting a context (must be loaded in memory) it would not continue reading from rabbit when it starts Flow interface fix: When inside the configuration from the Rabbit Receiver unit, the queue configuration is generated with an extra indent level (mqs.mqs and is mqs), which doesn’t properly configure the unit Output event bug fix in Rabbit Receiver unit: When setting a field for channel pilot, inputting the “Channel” object causes an error
Related products:Devo Platform
NewsJul 21, 2022
SecOps Release 3.3!
Update 3.3Region Status CA Released US Released EU Released APAC Released In this release, several new features and functionalities in the Security Operations investigations and triage tabs were released. These accelerate the workflow of the SOC team and simplify your interactions with the Security Operations solution. New features Artifact storage in investigations for improved analysis and incident response coordination. Ability to add custom fields in the investigation for linking with third-party systems. Support of markdown and text formatting in alert annotations and investigation comments. Ability to change status of alerts from the Triage page (grouped by entity and not grouped views) for improved workflow. Human readable text in the Extra Data field in alert details so you can read the data easily, as well as copy and paste it to other systems. Improved Error Communications specifying what analysis went wrong. New Dialog design, consistent in the entire application. Bug fixes Isnotnull function was fixed, when running the alerts through SecOps. Fixed CrowdStrike settings issue that was not enabling to perform CrowdStrike Falcon enrichments. Delete enrichment in investigation detail is fixed. Users can now upload the same file twice in an investigation. Loading layer in real time for triage and investigation: performance issues are fixed. We fixed the alert associations tab in investigations which was not updated correctly when you delete the latest alert in the investigation.
Related products:Devo SecOps
NewsJul 19, 2022
Alert Pack 2 for Devo Platform Released!
The Devo SciSec Team (Devo’s Threat Research Team) has released our second alert pack in all Devo domains! This alert pack brings our SecOps related content to our non-SecOps customers and can help jumpstart threat coverage. Inside of this pack we have a plethora of detections that will alert when an attacker is using common reconnaissance tactics. These tactics are ones that are often some of the first used to help the attacker get a layout of the environment they intend to attack. Complete information on this threat vector. More detail from the Mitre organization:Reconnaissance consists of techniques that involve adversaries actively or passively gathering information that can be used to support targeting. Such information may include details of the victim organization, infrastructure, or staff/personnel. This information can be leveraged by the adversary to aid in other phases of the adversary lifecycle, such as using gathered information to plan and execute Initial Access, to scope and prioritize post-compromise objectives, or to drive and lead further Reconnaissance efforts. Download now directly from Devo Exchange by clicking here. Full release notes and details of every alert in this Alert Pack. Inside of this pack we have these alerts that cover multiple technologies, including the most commonly attacked technologies:SecOpsFWIpScanExternal: Alerts when an outsider tries to scan firewall ports.SecOpsFWExcessFirewallDenies: Alerts when there is excessive and rapid firewall denies. Often used to try and find an open port within a firewall.SecOpsFWPortScanExternalSource: Alerts when an outside source is scanning the firewall looking for open ports.SecOpsGCPPortScan: Alerts when an attacker is scanning your GCP environment for open ports.SecOpsVpcNetworkScan: Alerts when an attacker is scanning the network.
Related products:Devo Platform
NewsJul 8, 2022
Release 5: Out of the box Alerts
Sec-Ops is proud to present the industry leading Release 5 Available in the Security Operations application.The Devo SciSec Team (Devo’s Threat Research Team) has released more out of the box detections for the Devo Security Operations Content Stream.Release 5 bring the total number of out-of-the-box detections to 355 and making Devo the market leader in ready to use detections for Microsoft Azure!This latest release continues Devo’s emphasis on Cloud Security Monitoring as a key use case, containing a large number of detections for Azure, Office 365, and Google Workspace. Additionally, Devo has expanded its out of the box coverage for Windows, and AWS, which are commonly ingested into Devo and critical for maintaining security monitoring.Head on over to our Docs to view full release notes! Here is a sample of 5 of the new alert descriptions:A Google Access Transparency log event has been generated. Google is accessing your data. An adversary may steal application access tokens as a means of acquiring credentials to access remote systems and resources. A government-backed attacker could try to steal a password or other personal information of one of your users by sending an email containing a harmful attachment, links to malicious software or to fake websites. An attacker could steal the credentials of one of your users. An attacker could steal the credentials or the mobile device of one of your users.See the full release notes here.
Related products:Devo SecOps
Jul 7, 2022
Devo Platform Release 7.13
Platform release 7.13New Stat Count Tool: Improvements to the UI Other Enhancements in 7.13 Region Status CA Released US Released EU Released APAC Released New Stat Count Tool:Devo has added a new tool, Stat Count, to Data Search, which allows users to compute statistics on the values of the columns in your query results. This gives users the ability to instantly compute and analyze data with the click of a button. Access Stat Count in Data Search by clicking on Tools→ Stat Count: Stat CountStat Count has four main panels: The Statistics Panel, the Edit List Panel, the Bulk Reports Panel, and the Details Panel. Statistics PanelThe Statistics panel shows the estimated values for the fields you select. Exact values are computed at the time you generate a Bulk Report. Bulk ReportsThe Statistics panel also includes a progress meter bar that shows the percentage of the data scanned and a cancel button to manually stop the compute operation. A search box is provided to locate columns quickly. Clicking the three dots button will allow the user to save the current column configuration for future searches over the current data table for that user. It can also reset the column configuration to the default value. Clicking the Edit List button launches the Edit List Panel. Edit List PanelThe Edit List panel allows you to quickly select columns returned in your query and view their data types. Notice that the Edit List panel also has a search box to search and locate the columns you need quickly. The SAVE button will return to the Statistic panel displaying only the checked columns. The “~” on the Statistic panel denotes that the following values are statistical estimations. To obtain exact value counts, perform a bulk report by clicking on the Bulk Reports and Generate buttons. Statistics Panel → Bulk ReportsThe Bulk Reports panel generates exact statistics for the values in the selected columns. Like the Statistics Panel, it also has a search bar to locate columns quickly. Clicking the Generate button will run an exact, updated calculation on the values for the selected columns.The fourth and final panel is the Details Panel which shows details of the individual column you’ve selected. You can access the Details Panel by double clicking on any item you’ve selected in the Edit List panel: Details PanelThe detailed statistics show the number of occurrences corresponding to each top value for the selected column. If “Top values = Exact,” the top 10 values matching the exact counter are displayed. If “Top values = Estimated,” the top n values of the exact/estimated counter are displayed. The Exclude null selector allows you to exclude null value returns. The Add to favorites button will display extra statistics relative to the distribution of the top values: Add to FavoritesThe extra stats display enables users to determine which values have the most significant distribution and, thus, are the most relevant.To control access to the Stat Count Tool, we added a new role permission, “Stat count of searches” (Data search → Search Window), to enable the Stat Count Tool in Data Search:Stat count of SearchesPLEASE NOTE that Stat Count is only available in the SELF domain by default. To enable it across the entire domain, you must request it from Devo Support. Improvements to the UI We also added a time picker to the “Finders” and “Free text query” windows so you can select the time range for the query. This allows the user to easily select an exact time range instead of relying on the default time period. FinderFree text queryImprovements have also been made in the “Operations Over Columns” form with a new feature that allows users to add nested operations in the same step. This simplifies the process of creating complex queries. Create ColumnThese new features are available under the CREATE COLUMN, FILTER, and AGGREGATE tabs. Nested operations can be applied to the main operation arguments and the main operation result. Nested operations must use a single (unary) argument whose type matches the current nested operation argument.The 7.13 Platform release also brings improvements to the JSON Extractor in Data Search. In previous releases, the names of the extracted columns were a generic “usrcolX.” In 7.13 and onward, the whole path key of the source JSON field will be used. Additionally, the user will be able to modify the auto-extracted name by prepending the source JSON column name or removing the full path to the source JSON field, as shown by the checkboxes in the following example: Selected CellOther Enhancements in 7.13We removed the green horizontal scroll at the top of Data Search, as it was redundant with the standard scroll at the bottom of the screen. This offers slightly more screen space. The font has been changed to monospace in both query editor and table results. This updated format increases readability Null values are now displayed in italics to easily distinguish them from the “null” string All numbers are now aligned to the right to make it easier to compare values We added two new date operations in Data Search: “weekofyear” and “weekofmonth” We added two new aggregation operations in the Query Editor for eventdate: “min” and “max” Improved Finders display of Union Tables are now sorted alphabetically
Related products:Devo Platform
Filter by product
- All products
- Devo Platform
- Devo AI Assist
- Devo Exchange
- Devo Cloud Collector
- Devo Integrations
- Devo Relay
- Devo ThreatLink
- Devo SOAR
- Devo SecOps
- Devo Behavior Analytics
- Devo DeepTrace
- Devo Learning Hub
- Devo Documentation
Enter your E-mail address. We'll send you an e-mail with instructions to reset your password.
Scanning file for viruses.
Sorry, we're still checking this file's contents to make sure it's safe to download. Please try again in a few minutes.
OKThis file cannot be downloaded
Sorry, our virus scanner detected that this file isn't safe to download.
OK